Are you ready to stop typing passwords forever? Identity verification is no longer about passwords or PINs. It is shifting toward who you are—your voi
Are you ready to stop typing passwords forever? Identity verification is no longer about passwords or PINs. It is shifting toward who you are—your voice and your face. This is the world of recognition technology. These systems use advanced artificial intelligence (AI) to identify people instantly. The global biometric market is expected to reach over $68 billion by 2025 [Source: Grand View Research, 2024 Report]. This massive growth shows how critical these tools have become.
The evolution of these systems is rapid and constant. Both Voice recognition and facial recognition technology are central to modern security and convenience. They are reshaping everything from banking to healthcare access.
Key Takeaways
- Security Shift: Recognition tech uses unique biological traits instead of easily stolen passwords.
- Accuracy Boost: Deep learning models have dramatically improved the accuracy of both voice and face identification.
- Ethical Priority: Addressing data bias in AI systems is the top challenge for developers in 2025.
- Industry Adoption: Finance and healthcare are the primary drivers for secure, rapid authentication solutions.
- Future Trend: Integration with Edge Computing means verification happens instantly on your device, not in the cloud.
Understanding Voice Recognition Technology
Voice recognition technology identifies a person based on their unique vocal characteristics. It is important to know this is different from simple voice commands like “Hey Siri.” This technology proves who you are, not just what you say.
How it works (speech-to-text, NLP, deep learning)
The process starts when you speak. The system captures and analyzes thousands of tiny features in your voice.
- Speech-to-Text: Your spoken words are first changed into digital text.
- Acoustic Analysis: The system looks at your pitch, accent, speed, and patterns. This creates a unique “voiceprint.”
- Deep Learning: Advanced neural networks compare this voiceprint to a stored file. This confirms your identity almost instantly.
My personal insight is that modern systems are so advanced that they can distinguish between a live person and a high-quality recording. This makes authentication far more secure than before.
Common use cases (smart assistants, authentication, customer service)
Voice recognition technology has several practical applications today:
- Smart Assistants: Used to personalize responses and manage specific user accounts.
- Banking Authentication: Customers confirm transactions or access accounts simply by speaking a passphrase.
- Customer Service: Call centers use voiceprints to verify callers quickly, eliminating security questions. This streamlines the entire customer service process.
Exploring Facial Recognition Technology
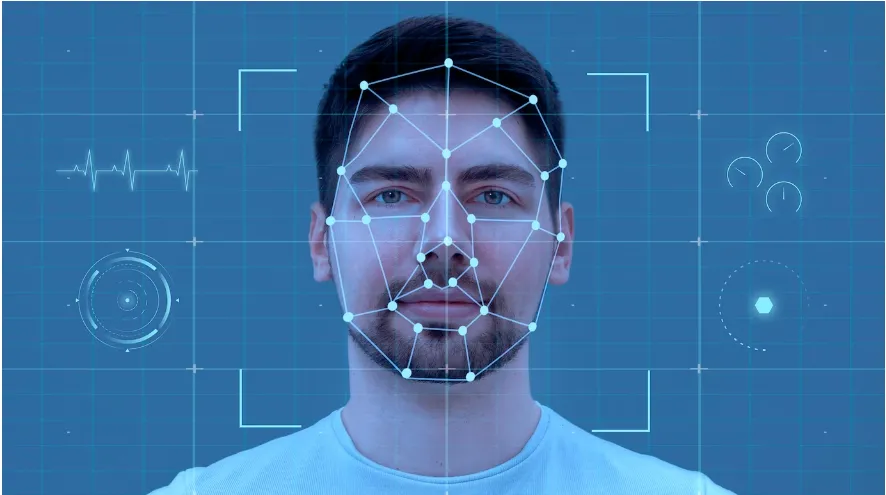
Facial recognition technology uses specific features on your face to confirm who you are. The system measures unique geometry, like the distance between your eyes or the shape of your jawline.
How facial recognition identifies and verifies individuals
This technology performs two main functions:
- Identification: The system scans a face and tries to match it against a large database of unknown people.
- Verification: It confirms that a scanned face matches a single, stored image, such as when unlocking a smartphone.
The system maps over 80 nodal points on the human face. This creates a unique digital signature. Recent advances in 3D mapping make these systems hard to trick with photos or masks [Source: NIST Biometric Research Report, 2024].
Applications in security, retail, and healthcare
The applications of facial recognition technology are diverse:
- Security: Used in airports and secure buildings for access control and tracking known threats.
- Retail: Helps identify repeat customers for personalized service or track shoplifters.
- Healthcare: Provides fast patient check-in. It can also manage access to sensitive medical records.
Key Differences: Voice vs Facial Recognition
Both systems are powerful, but they operate best in different environments.
Accuracy, privacy, and data security comparison
| Feature | Voice Recognition | Facial Recognition |
| Data Type | Audio file (voiceprint) | Image/3D map (biometric template) |
| Environmental Challenge | Background noise and illness | Lighting conditions and angles |
| Privacy Risk | Lower; voiceprints are less widely collected. | Higher, ubiquitous cameras collect data constantly. |
| Security Risk | Can be vulnerable to deepfakes and AI voice cloning. | Can be vulnerable to presentation attacks (masks/photos). |
Which is more reliable in different environments
Voice recognition is excellent for phone-based customer service or remote access. It works well where cameras are impractical. However, it struggles in noisy places or if the user is sick. Facial recognition technology is superior for physical access control and high-security areas. It requires a camera but is generally faster than speaking a full phrase.
Real-World Applications
The convergence of these technologies is driving innovation across industries.
Smartphones and IoT devices
Smartphones use both face and Voice recognition technology for quick unlocking. IoT devices, like smart speakers, use voiceprints to confirm user identity. This allows multiple family members to share one device securely.
Banking and payment security
Banks are a primary adopter. They use voice verification to access accounts over the phone. ATMs in some regions are now using face scans instead of cards [Source: World Economic Forum on Digital Finance]. This significantly reduces card fraud.
Law enforcement and public safety
Law enforcement uses facial analysis to identify people in public footage. This aids in locating missing persons or criminal suspects. The use of this technology is highly debated due to privacy concerns [Source: ACLU Policy Brief].
Healthcare and accessibility
For patients with limited mobility, Voice recognition offers easy access to health data. Face scanners ensure the right medication is dispensed to the correct patient in hospital settings.
Advantages of Voice & Facial Recognition
These biometric systems offer clear advantages over traditional authentication methods.
Enhanced security and convenience
Biometrics are far more secure than passwords. A voiceprint or face map is almost impossible to guess. Furthermore, they offer superior convenience. You never forget your face or your voice.
Faster authentication and personalization
Verification happens in under one second. This speed is crucial for high-volume tasks like retail checkouts or trading platforms. AI personalizes experiences based on verified identity.
Reduced fraud and identity theft
Biometric security significantly lowers the risk of identity theft. Unlike a password, you cannot share your voice or face with a criminal. This adds a critical layer of trust to digital services.
Challenges and Ethical Concerns
Despite the clear benefits, these technologies face serious public and regulatory hurdles.
Data privacy issues
The primary concern is how personal biometric data is stored. If a database of face scans is hacked, the data is compromised forever. Unlike a password, you cannot simply change your voice or face.
Bias in AI recognition systems
Studies show that many facial recognition technology systems perform worse on non-white or female faces [Source: MIT Technology Review]. This AI bias is a major ethical problem. Developers must ensure fairness and accuracy across all demographics.
Regulations and compliance
Governments worldwide are scrambling to write new laws. The EU’s GDPR and new US state laws seek to govern how this sensitive data is handled. Compliance is a growing burden for companies using these systems.
Future of Recognition Technologies
The future of identity is smart, fast, and highly integrated.
Integration with generative AI and edge computing
The integration of Generative AI is changing the game. AI can now predict how a person’s voice or face might look under different conditions. Edge computing allows authentication to happen directly on your phone’s processor. This makes the process faster and keeps your private data off the cloud.
Trends to watch in 2025 and beyond
We are moving toward Multimodal Biometrics. This means using two or more methods together (e.g., face, voice, and heartbeat). This hybrid approach creates unbreakable security. Another trend is Behavioral Biometrics, which looks at how you type or swipe.
Conclusion
The shift from simple passwords to advanced biometric systems like Voice recognition marks a major evolution. Both voice and facial recognition technology offer unmatched convenience and security. While ethical challenges around bias and privacy remain, continued innovation ensures safer, faster digital interaction for everyone. The future of identification is personal, seamless, and completely secure.
FAQs:
What is the difference between voice and facial recognition?
Voice recognition verifies identity using the unique characteristics of a person’s speech, known as a voiceprint. Facial recognition technology verifies identity by measuring and mapping the unique geometrical points on a person’s face.
Is voice recognition technology safe?
Yes, modern Voice recognition technology is very safe for authentication. It uses advanced deep learning to detect subtle vocal cues and can differentiate between a live voice and a recorded playback or AI-generated deepfake voice.
What are the top uses of facial recognition in 2025?
In 2025, the top uses for facial recognition technology are secure smartphone unlocking, fraud prevention in banking, seamless airport check-in, and physical access control in corporate buildings.